Authentication using SSH keys and disabling password access
How do I set up access to the server using SSH keys and disable password authentication?
What is SSH key authentication, how does it work and what is it used for?
Authentication using SSH keys is an extremely secure way to log in to the server. In this case, two cryptographic keys are used, each key pair consists of a public and a private key. The public key can be distributed without fear, because it serves to encrypt messages that can only be decrypted with a private key.
The private key must be stored very securely! We highly recommend that you protect it with a passphrase as an additional precaution.
You can add a public key in the "My Servers" section, the "SSH keys" tab.
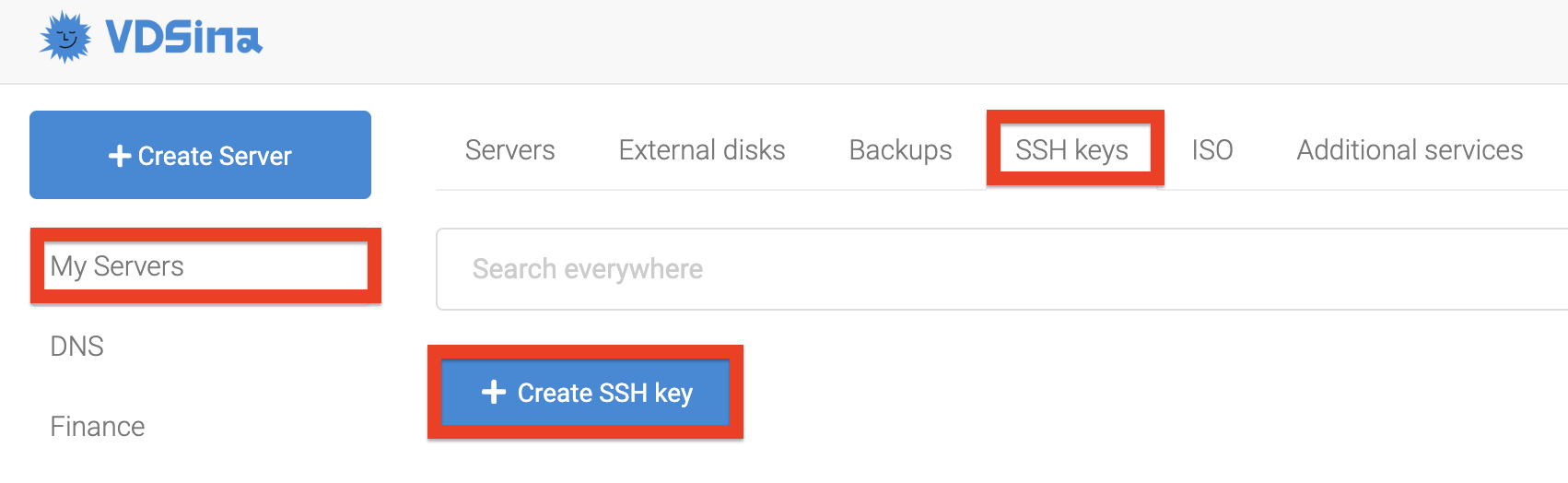
It is possible to add several keys at once
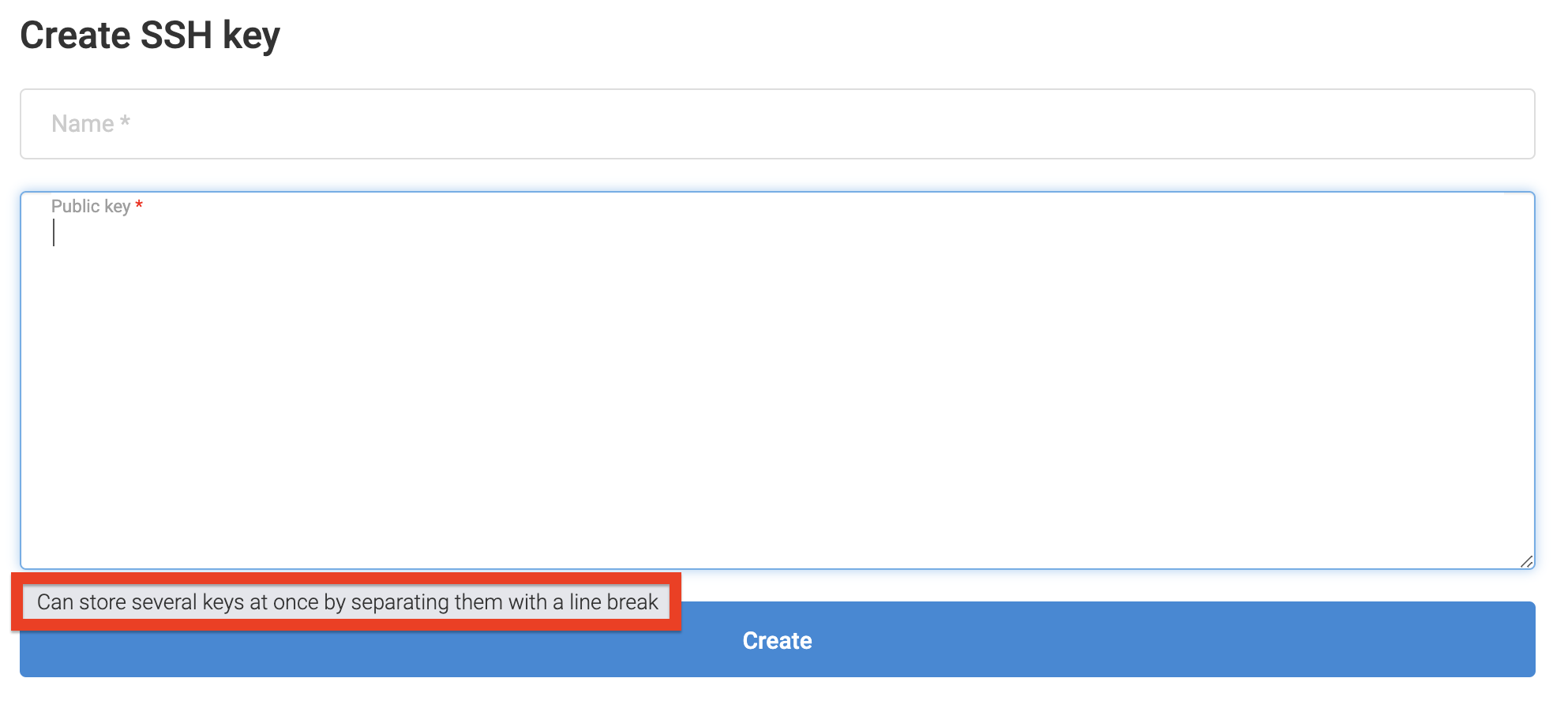
Later, when ordering a server, you can select this key.

If you have configured access using SSH keys on your server, the panel will automatically upload the public key to the ~/.ssh/authorized_keys file on your server. When the user tries to connect to the server using SSH keys, he checks the client for the presence of a private key. This is how authentication takes place.
How do I generate keys?
In Windows, this can be done using Putty, download the program and run the file puttygen.exe . Select the key type RSA, and the length is 2048 bits, click Generate, and when generating, randomly move the mouse cursor.
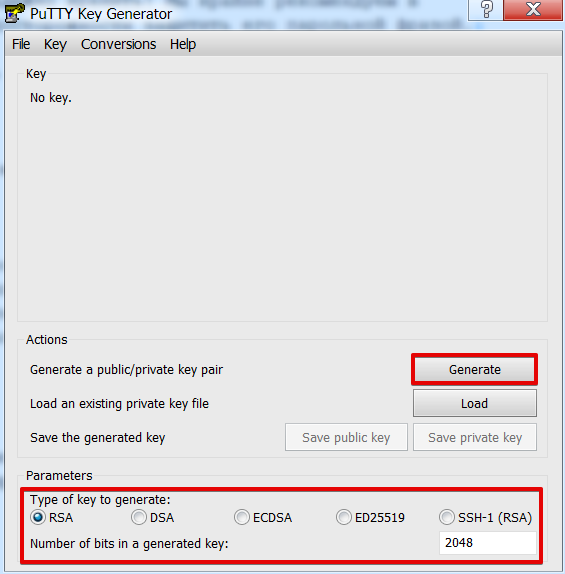
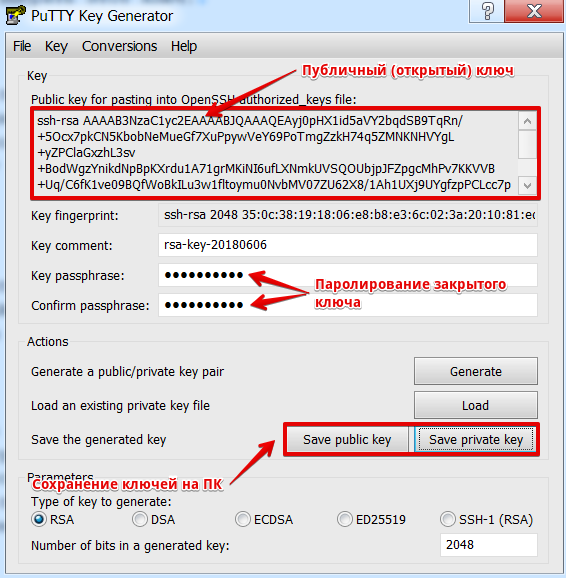
Save the generated key pair on your computer. To do this, use the Save public key and Save private key buttons. Do not forget to protect the private key with a secret phrase/password (you must enter in the Key passphrase/Confirm passphrase field). Copy the generated public key and paste it into the appropriate field of our control panel. Use the same program in the future to connect with the generated key.
On Linux or macOS, open a terminal and run the following command
ssh-keygen -t rsa
You will see the following computer response
Enter file in which to save the key (/root/.ssh/id_rsa):
You need to press the Enter key and enter a phrase / password for additional protection of the private key, the system will ask you to enter it 2 times
Enter passphrase (empty for no passphrase):
After that, the key will be created, and a message with approximately the following content will be sent to the console
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
bf:9b:79:ca:9f:96:bb:4c:b9:67:e9:e6:4d:1f:30:e1 root@xxx.vdsina.ru
The key's randomart image is:
+--[ RSA 2048]----+
| |
| |
| . |
| . . |
| S E |
| . .o |
| . o. o.|
| . *+o=oo|
| B*BOo o|
+-----------------+
To get the public key, enter the command in the terminal
cat ~/.ssh/id_rsa.pub
Enter the received key in the appropriate field of our control panel. In the future, you will be able to connect from your PC to the server using the command
ssh root@[IP-адрес сервера]
Additional server protection when using SSH keys: disabling password authentication
Attention! Before performing this step, be sure to check the operation of SSH keys and login to the server using them.
If you managed to connect to the server using SSH keys, then as an additional security measure, you can disable password authentication. To do this, open the SSH daemon configuration file /etc/ssh/sshd_config (/etc/ssh/sshd_config.d/50-cloud-init.conf for Ubuntu 22.04) and uncomment the PasswordAuthentication directive, set it to no.
PasswordAuthentication no
Save the changes and restart the service
# Ubuntu/Debian
sudo systemctl restart ssh
# CentOS/Fedora
sudo service sshd restart



